Analyzing the Petya Ransomware Attack: Why It Could Be Your Fault

After the obvious hustle-bustle of last month’s WannaCry Ransomware Attack, there is global chaos with yet another cyberattack – Petya Ransomware Attack.

After the obvious hustle-bustle of last month’s WannaCry Ransomware Attack, there is global chaos with yet another cyberattack – Petya Ransomware Attack.
Petya Ransomware Attacks is a version of the Petya attack, which was designed with the sole purpose of making money. It is designed to spread fast and cause extensive damage.
Although there is significant code sharing, the real Petya was a criminal enterprise for making money – The Grugq
Petya is using EternalBlue, a leaked NSA hack that was also used by WannaCry to infect over 150 countries. It spreads through a weakness in Windows SMB.
This malicious software has spread via large firms including the advertiser WPP, food company Mondelez, Danish shipping and transport firm Maersk, and legal firm DLA Piper.
If you hadn’t patched your systems even after WannaCry global disarray, this was bound to happen.
Windows update for the Eternal Blue exploit is given by Microsoft already and should be patched by now.
If you don’t know how to get the security patches, get it done here.

But it might not be just your fault
Here’s why…
There are indications that Petya is deadlier than Ransomware attacks and may have other tricks to spread.
Other than EternalBlue vulnerability, Petya uses two Windows administrative tools.
For instance, as per the former NSA analyst and cybersecurity entrepreneur David Kennedy, this ransomware attack finds passwords on the infected computer to move to other systems.
This is done by extracting passwords from memory or from the local filesystem.
If one doesn’t work, it tries the next one. Well, it definitely has a better mechanism than WannaCry.
As per Russian security firm Group-IB, Petya uses a tool called “LSADump” that gathers passwords and credential data from Windows Computers and domain controllers on the network.
New #Petya uses #LSADump to get Admin password and infect all network. There is no need for #EternalBlue vulnerable PCs. #infosec
— Group-IB (@GroupIB_GIB) June 27, 2017
When Petya ransomware infects Windows PCs, it encrypts all the user data, and the computer displays a note demanding $300 Bitcoins (digital currency) to gain access.
However, don’t pay the ransom.
Yes.
It wouldn’t help you retrieve your data/files.
There are two reasons:
You Might Be Safe If you see…
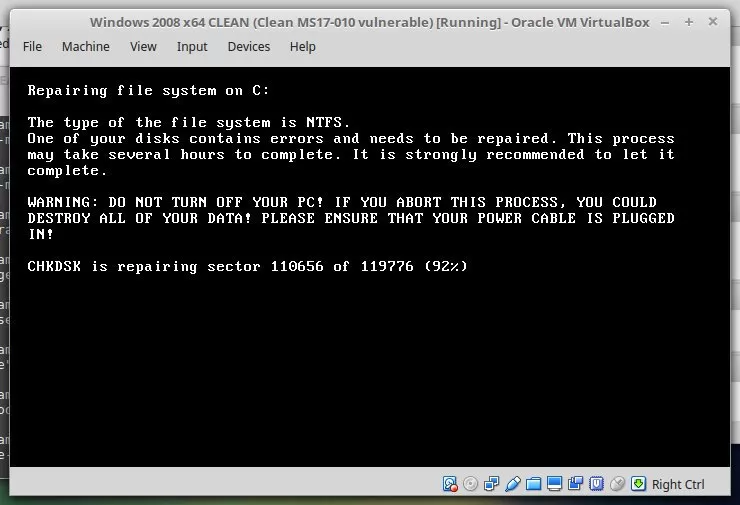
It encrypts ON BOOT.
If there is a message “CHKDSK”, your files are not yet encrypted.
Power off immediately and recover data with LiveCD.
You May Also Like: An Ultimate Magento Security Guide You Need
#1 Patch Your Systems
Just like WannaCry, Petya is also targeting a vulnerability in older Windows.
The best way to protect yourself is to update your Microsoft Windows. They have released a patch to protect against the vulnerability on the Windows XP system.
Thereafter, they have released more patches considering the high risk of cyberattacks.
#2 How to do it?
Enable Microsoft to automatically update your computer.
For older versions, go to The Microsoft Website and download patches. If you don’t know or don’t have the expertise, get assisted.
#3 Get Backups
It is 2023 and if you don’t back your files up, then you are surely going to face more attacks.
Copy your files to another location like in the cloud or an external hard drive. You can back up data more than once a month and it won’t cost you a penny!
#4 Protection Programs
Get protection programs that not only counter attacks but also notify you about the potential threat your computer might be facing. It includes firewalls, anti-virus programs, and other protective software.
#5 Be Cautious While On Public Network
Using a public network means you are visible to everyone else using that network. You can change the security settings on your system while using public Wi-Fi.
Use A VPN that hides your computer from others on that network. Although it won’t fight malware, you won’t be the target now.
#6 Bonus Tip
Have a Server Security Scan to detect any vulnerabilities or malware injected into your server.
There will always be a new virus, malware, ransomware, roaming around the web to find the next victim.
Your only option is to protect your website and assets. For that, you need secure Magento Hosting, with experience in web security.
If you have any questions, you can always ask in the comment section. 🙂
Check out the latest blog entries
MySQL Trigger is a code that triggers certain actions that should happen when the particular operation performs on the database. It means that the trigger tells the database to execute specific commands when a specifically mentioned event happens. The mentioned event could be an insert, update, or delete command.

Do you prefer to manage your servers on your own?